Banyan Federated SaaS Applications
Use Banyan's OIDC and SAML capabilities enforce Zero Trust policies on your SaaS applications
- Updated on Jan 10, 2024
This topic details Banyan Federated authentication (SAML and OIDC) to secure your SaaS apps; in this technique, the SaaS Application is configured for SAML/OIDC authentication using Banyan’s TrustProvider component and Zero Trust policies can be defined for each individual SaaS application. You can also configure IdP Routed authentication to secure your SaaS apps.
How It Works
The diagram below provides a conceptual overview of how you can use Banyan for Device Policies on SaaS Apps.
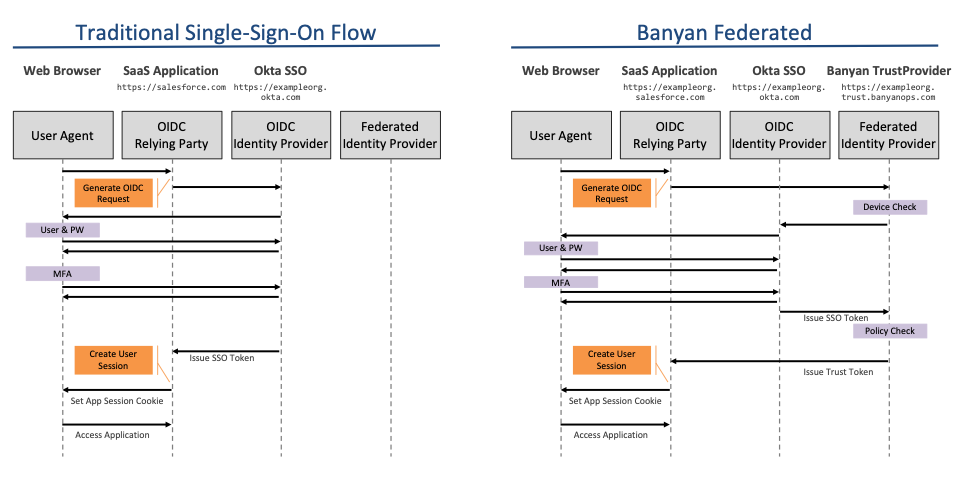
In the Normal Single-Sign-On flow, your SaaS application redirects to your Identity Provider to authenticate the user.
In the Banyan Federated authentication flow, you configure your SaaS application for SAML/OIDC authentication using Banyan TrustProvider. Banyan TrustProvider federates right back to your Identity Provider for user authentication but, because Banyan is now in the authentication flow, it is able to enforce Zero Trust security policy.
The step-by-step flow is detailed in the diagram below.
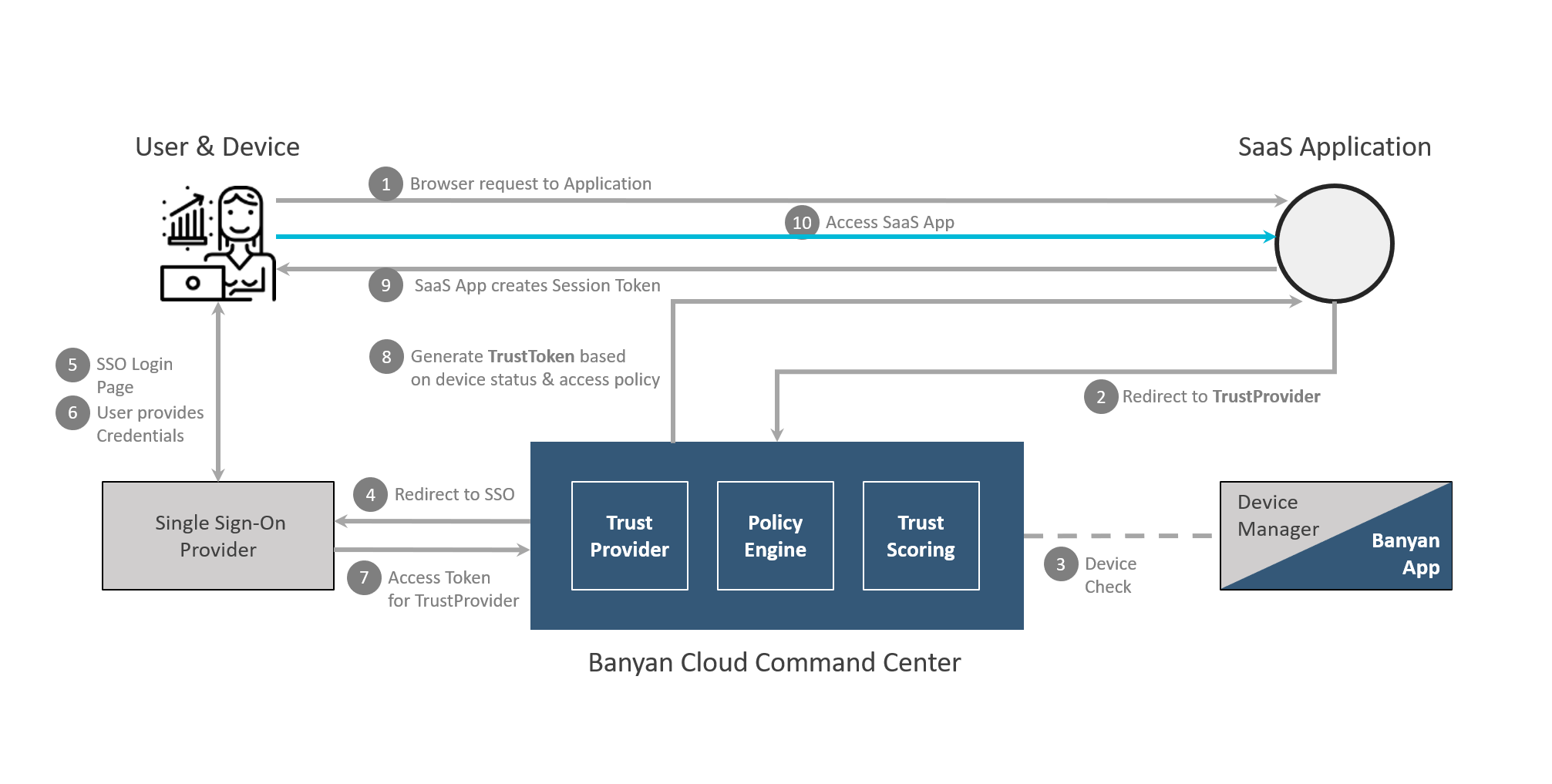
At a high level, Banyan Federated authentication flow involves the following steps:
- Register a SaaS App and configure it to point to Banyan first, via SAML authentication protocol.
- When a user attempts to access a Banyan-protected SaaS application, Banyan redirects the user to your IdP.
- Once the user authenticates with your IdP, the request returns to Banyan.
- Banyan enforces the configured Zero Trust Policies.
- If the device is compliant, then the user can access the SaaS application.
Limitations
Banyan’s OIDC implementation is standards-compliant and where possible you should use OIDC to set up your SaaS applications.
Banyan’s SAML implementation supports most SaaS application but there are currently a few key limitations, such as:
- SAML attribute mapping is not supported
- Email ID is the only supported Name ID format when not using Passthrough Name ID
- SAML single logout is not supported
- IdP-initiated SSO is not supported
- Encryption is not supported
Pre-requisites
In order to set up this integration, you need will need administrative access to your SaaS application, with the ability to add an external SSO Provider.
We also assume you have already created the application integration called “Banyan TrustProvider” following our instructions to set up an IdP as your Identity Provider.
Steps
1. In the Banyan Command Center, create a Policy to manage access to SaaS Apps
1.1 Navigate to Private Access > Access Policies > + Create Policy, and create a new Policy using the Web Policy template.
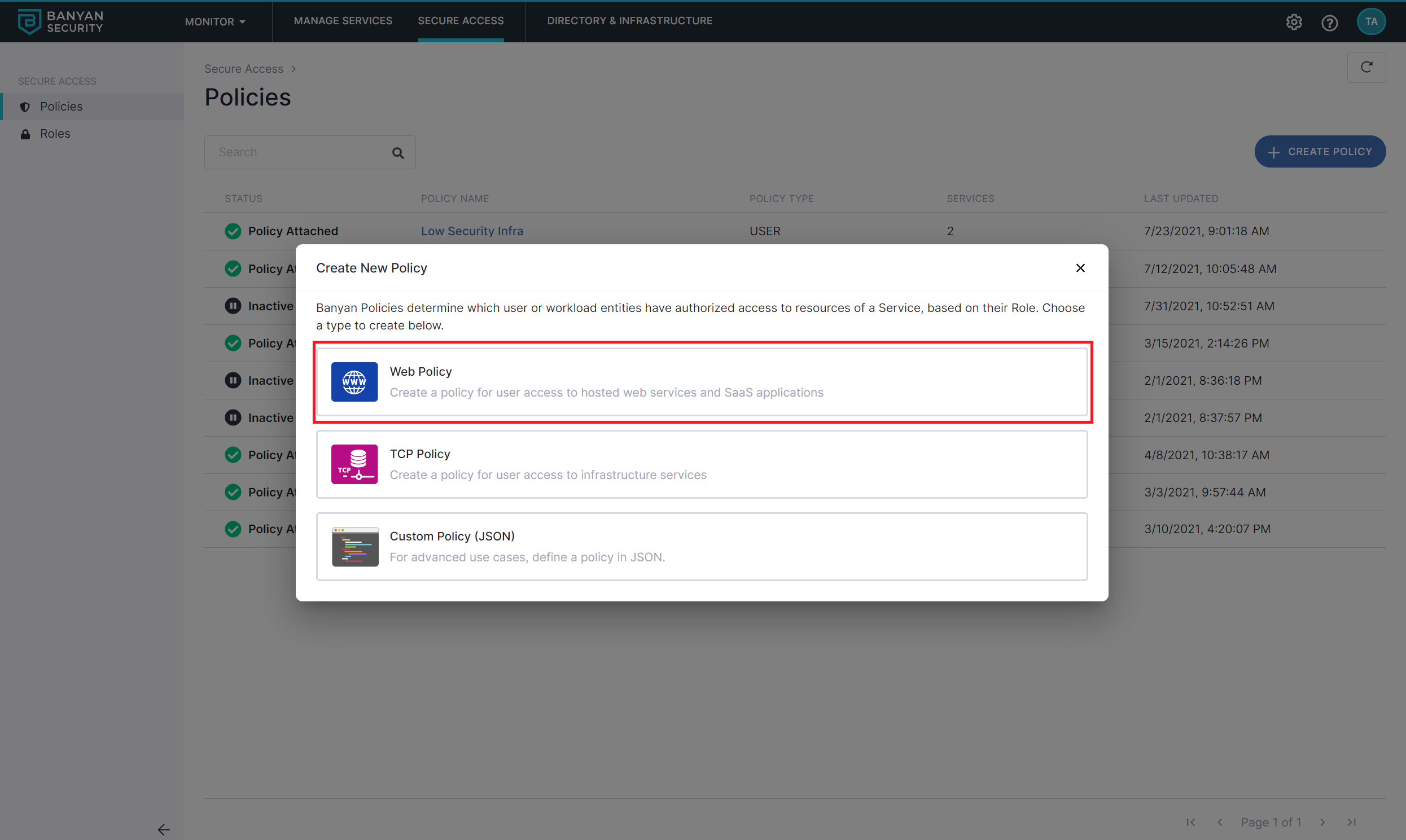
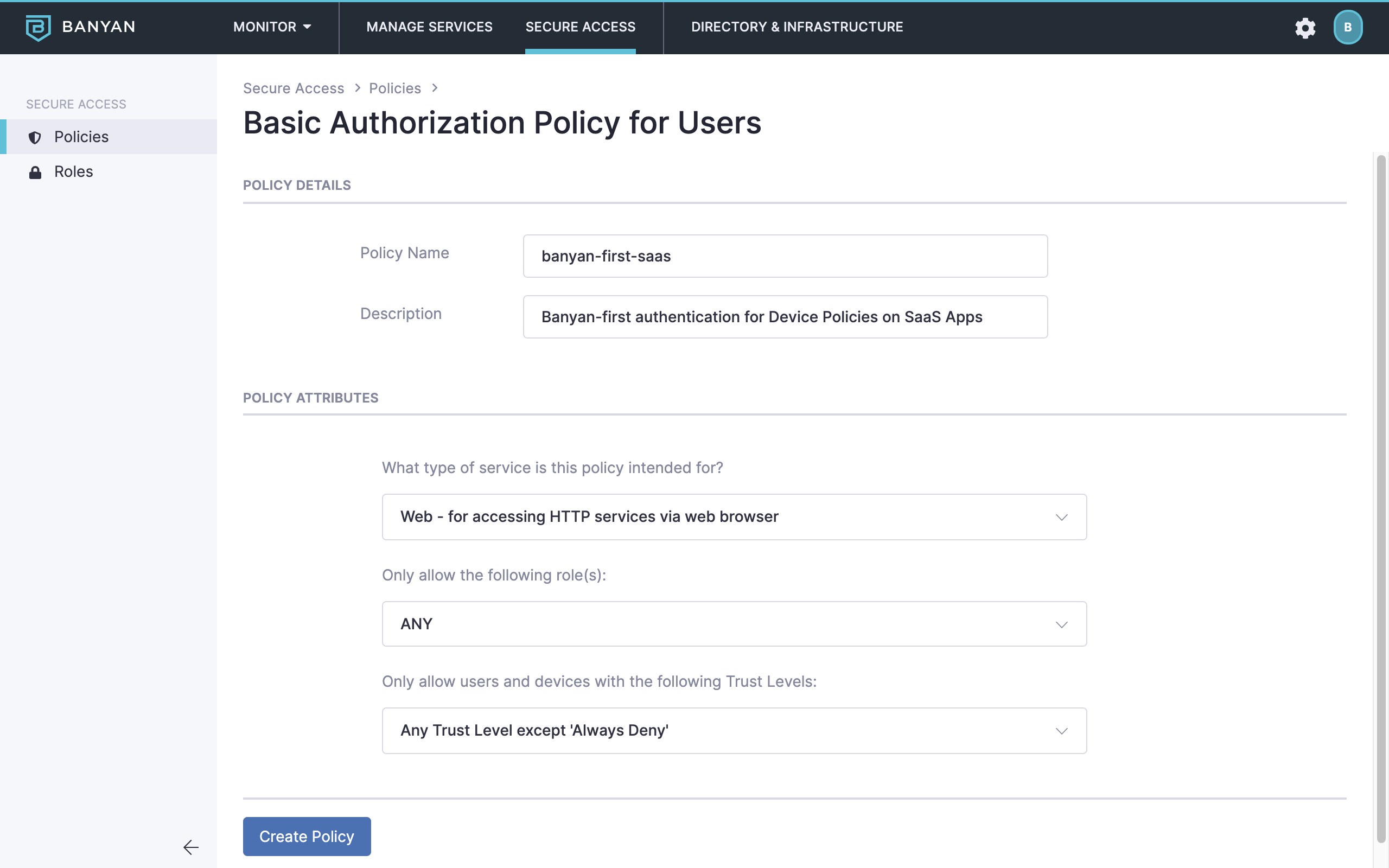
1.2 Name the policy banyan-first-saas.
1.2 Also set the policy attributes for minimal controls:
- allow access from user principals with
ANYrole - do not set a
Trust Levelrequirement
2. In the Banyan Command Center, register the SaaS App
2.1 Navigate from Internet Access > SaaS Apps, and then select + Publish SaaS Application.
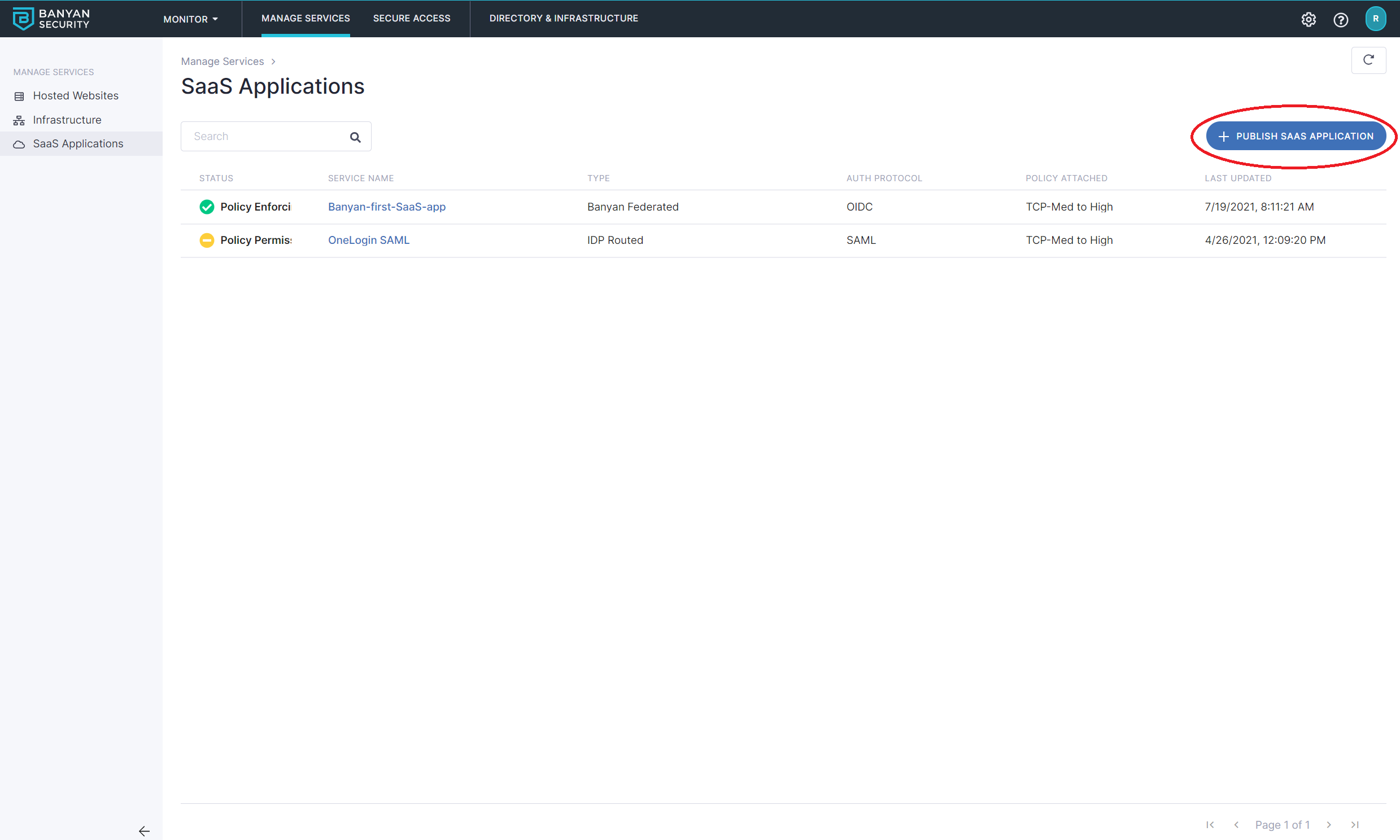
2.2 Select Banyan Federated for your application to be federated with Banyan.
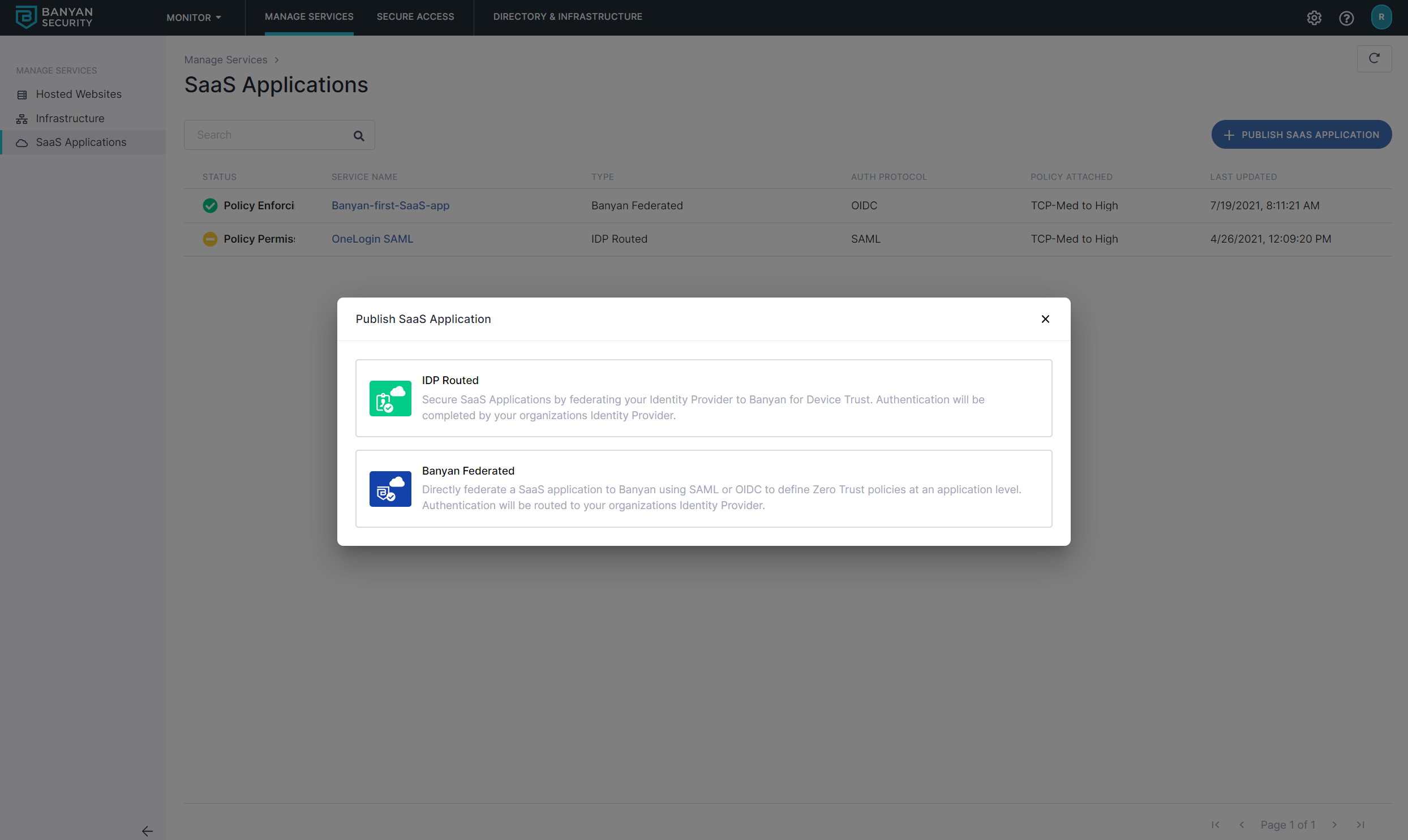
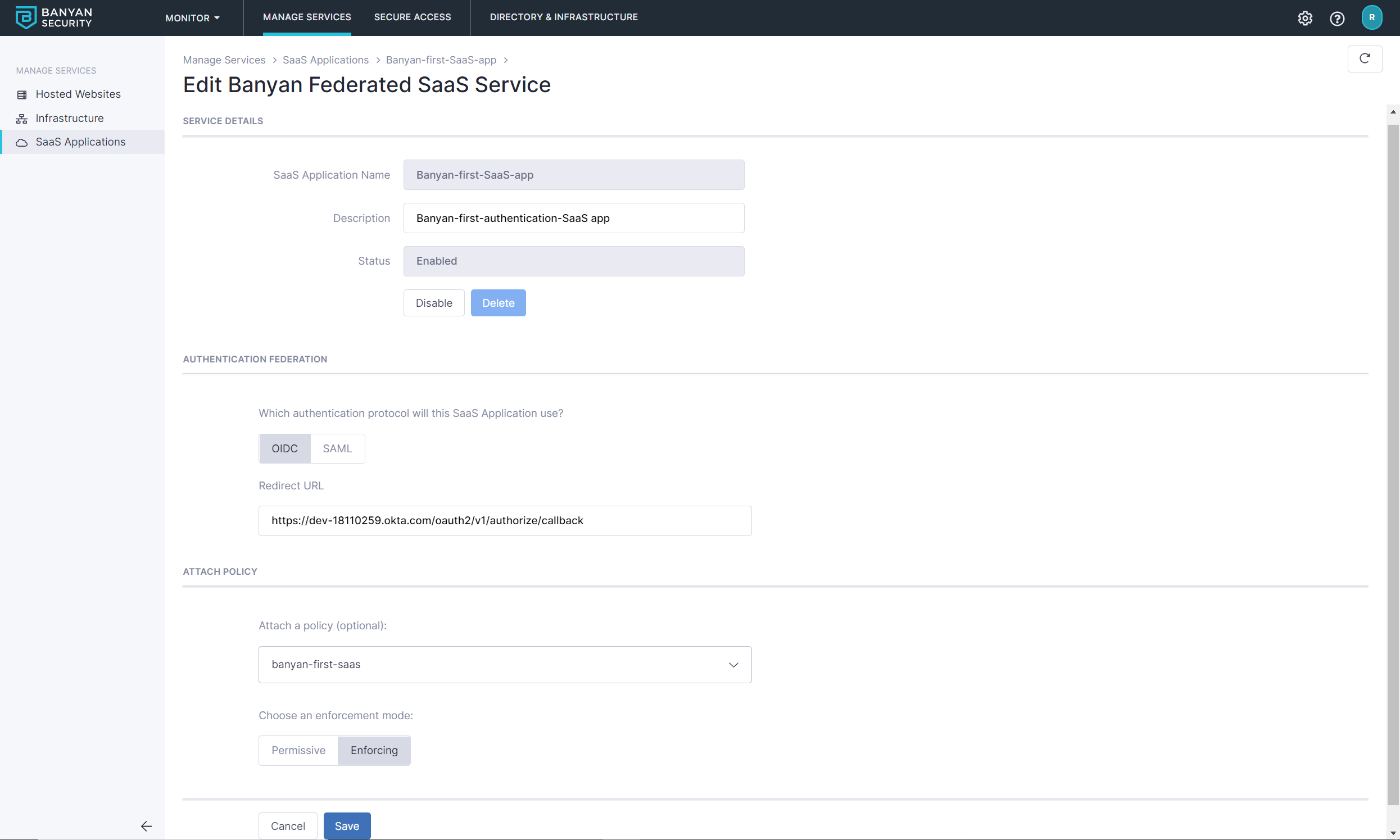
2.3 Name the SaaS App banyan-first-saas-app and then set the Authentication Federation protocol (either OIDC or SAML).
2.4 The Authentication Federation fields depend on the authentication protocol used by the SaaS App.
- If you are configuring OIDC, then enter:
- Redirect URL - Provided by the SaaS App
- If you are configuring SAML, then enter:
- Redirect URL (SAML ACS) - Provided by the SaaS App
- Audience URI (Service Provider Entity ID) - Provided by the SaaS App
- Name ID Format - Provided by the SaaS App. If none is provided, then select Unspecified
- NameID Value - Select the option according to your business needs.
- Use passthrough Name ID persists the NameID from your IdP
- Custom enables a NameID Custom Attribute field to enter an attribute supported by your IdP
Do not select Legacy compatibility mode if you are configuring a new SaaS App. This option is only intended to preserve existing SaaS App functionality and should not be used for new SaaS Apps.
2.5 Attach the banyan-first-saas policy we had previously created and set enforcement mode to Enforcing.
2.6 Once you have created this SaaS App in the Banyan Command Center, the next screen will give you the details you need to set up your Identity Provider to use Banyan to enforce your policies, depending on authentication federation (OIDC or SAML).
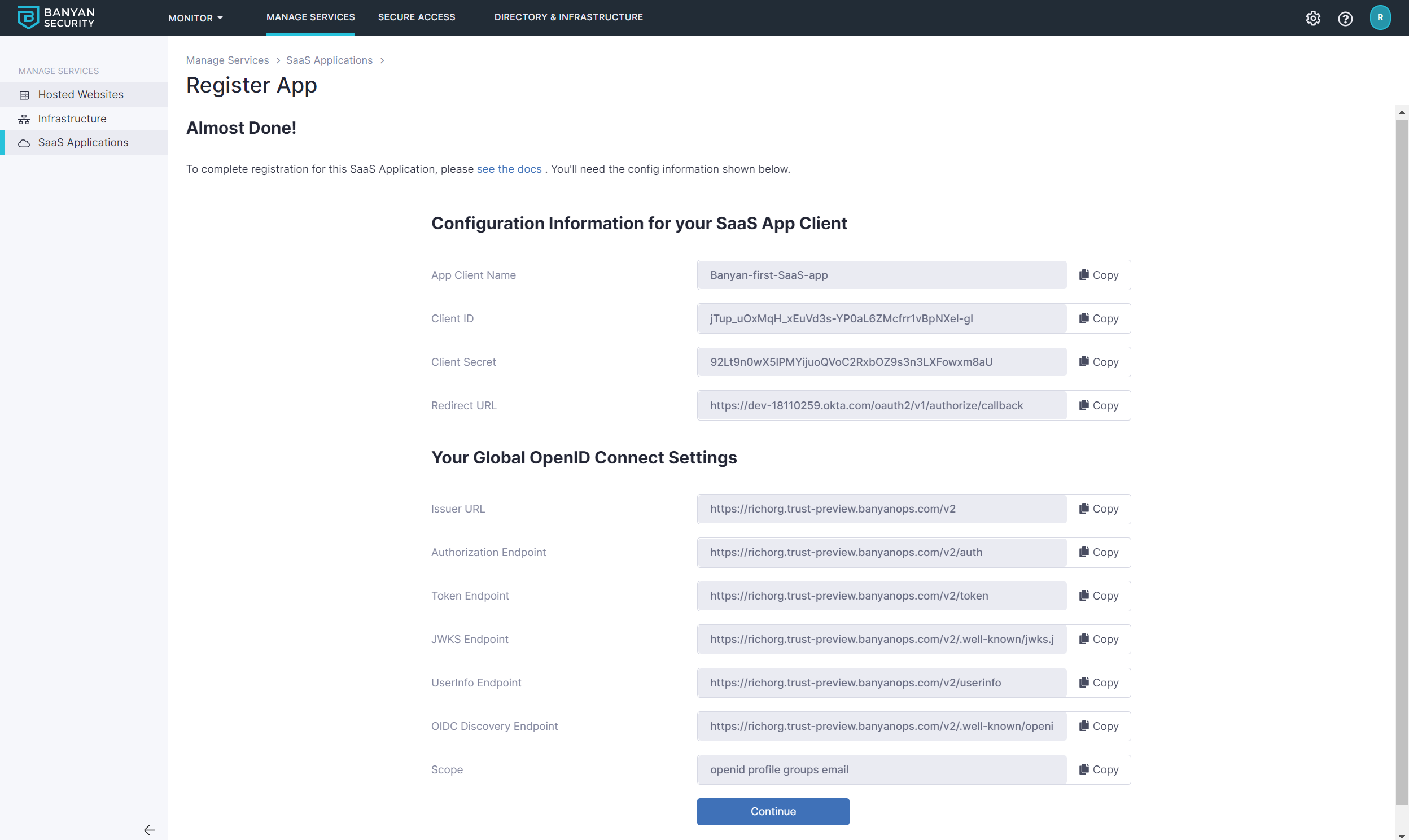
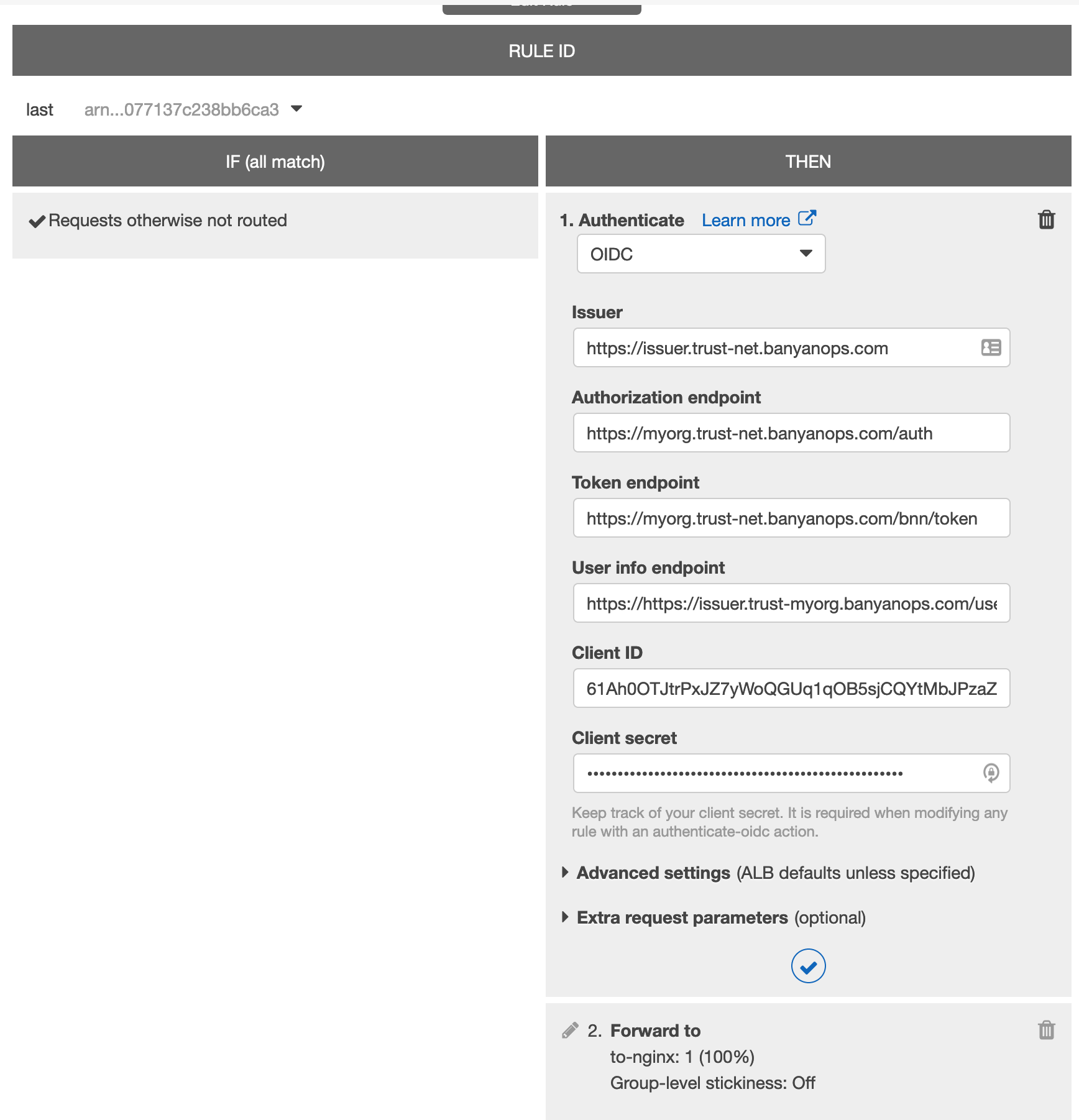
3. Configure your SaaS app to use Banyan for authentication
Fill in the data from Banyan Command Center for the SaaS application you are securing.
4. Test the SaaS app
Use a private/incognito browser window to navigate to the URL of the SaaS App you set up. You’ll see the request being redirected to Banyan TrustProvider and your security policies being enforced.
Great! You have created a Zero Trust policy for a SaaS App and accessed it securely using Banyan Federated authentication.
Troubleshooting
If you configured a SAML SaaS App and are unable to access it, then review your Banyan organization’s system log for events. The example below shows a request being denied because the SaaS App was configuring with an invalid custom NameID attribute (ASDFASDF).
{
"id": "caf0fd4b-8c71-4a3f-926b-631607b9fb79",
"org_id": "c121d8d8-f319-498c-b107-480be7cf5fea",
"org_name": "edgeorg",
"severity": "ERROR",
"action": "Deny",
"type": "Identity",
"sub_type": "UserPrincipal",
"message": "couldn't find expected attribute \"ASDFASDF\" from upstream idp. Valid options are [email_verified family_name groups locale name sub updated_at email given_name preferred_username zoneinfo]",
"result": "ERROR",
"created_at": 1604519771303,
...
}
In this scenario, double-check the attribute mapping in the Command Center and compare it to the format provided by your IdP. Fix any errors, then attempt to access the SaaS App until successful.
Can’t find what you’re looking for?
We’re happy to help. Contact our team.