Managing Discovered Public Resources
Use Banyan to secure your org's public resources
Discovered Public Resources Overview
IT and Security teams tend to have low visibility into devices that are not connected to their network, given that, traditionally, the point of visibility has been the office’s network gateway. This lack of visibility often results in applications being accessed that Security/IT teams haven’t reviewed or adequately protected.
Using Banyan’s Security Actions, admins can manage and protect discovered resources. Security Actions will vary depending on the particular app’s requirements.
Limitation 1: In certain Zero Touch Deployment scenarios which limit user info, the record of a device accessing an app might not be recorded.
Limitation 2: Apps are defined based on their domains and not based on their FQDNs.
Security Actions
Banyan offers the following Security Actions:
Identity Provider Federation
This topic details Banyan Federated authentication (SAML and OIDC) to secure your SaaS apps; in this technique, the SaaS Application is configured for SAML/OIDC authentication using Banyan’s TrustProvider component and zero-trust policies can be defined for each individual SaaS application.
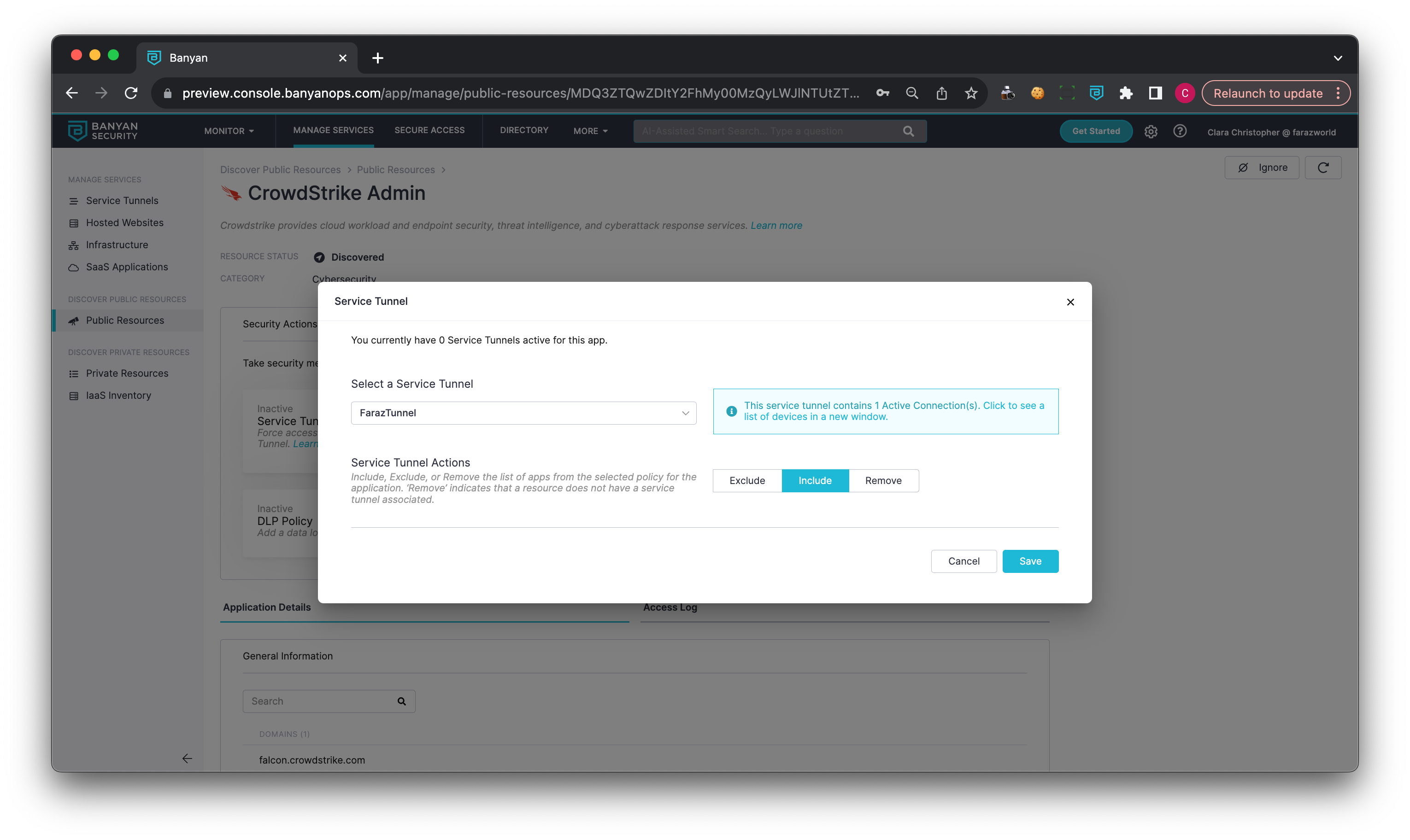
Service Tunnel Access
This Security Action allows admins to enable users’ access to the discovered app through a Service Tunnel, thus securing access.
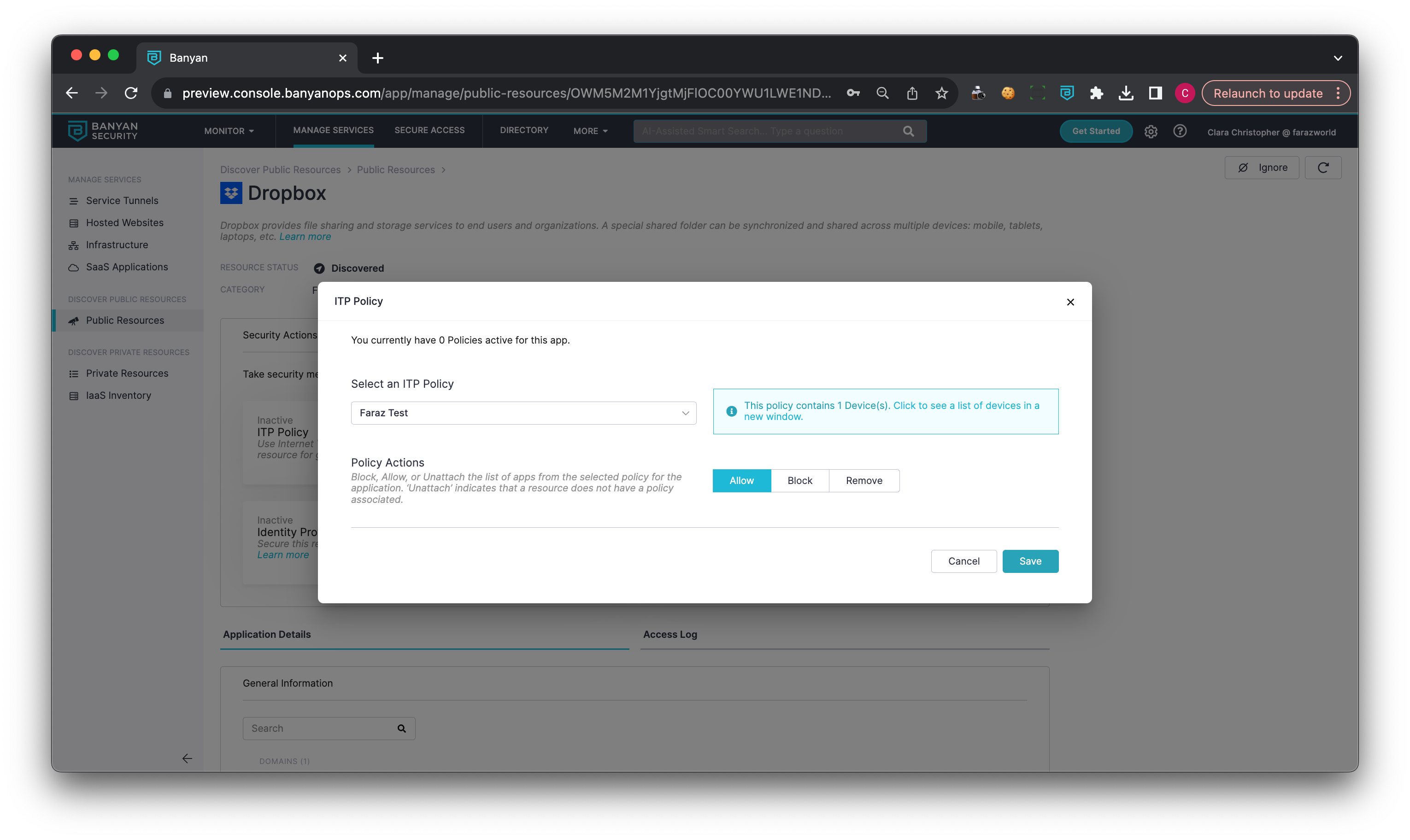
Internet Threat Protection (ITP) Policy
Enforcing an ITP policy on a discovered app allows admins to block specific users or groups from accessing this app.
Data Loss Prevention (DLP) Policies
Note: DLP policies are currently in early preview; contact your account team to have these features enabled in your organization.
Enforcing a DLP policy on a discovered app allows admins to monitor and manage unintentionally exposed data via text and file uploading and downloading rules.
Can’t find what you’re looking for?
We’re happy to help. Contact our team.